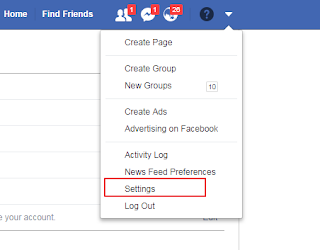
2. Tap Security and Login then select Use two-factor authentication.
3. Select the Code Generator and tap the third party app link.
4. After tapping the link, you will be redirected to Set Up a Third Party App to Generate Codes. A QR code will pop-up in the screen which will be use in the next step.
5. Now launch the Authy (android app) in your smartphone and tap the 3 dots in the upper right corner.
6. Select Add Account.
7. Select SCAN QR CODE.
8. Scan the QR code in step #4.
9. Successfully your FB account now is already safe and secure. Create now your desired account name in the Authy then click DONE.
10. Now everytime you login in any unrecognized device you will be ask to enter the login code to continue accessing your FB account.
11. Authy will provide you the login code for you to continue. Note: every codes will expire within 60 seconds. After the 60 seconds grace period the codes provided will not usable anymore.
DONE!!!
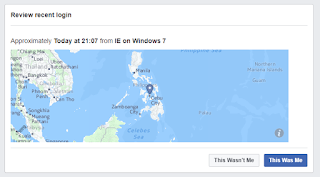
If someone trying to login using your FB account without your consent, a facebook notification will pop-up in your device.
You have also the option to review your recent login made in your device.
Keep your account always SAFE..
WARNING!!!
Siguraduing hindi mawala ang smartphone mo or huwag itong manakaw or iwasang masira ito dahil kung ito'y mangyayari sa hinaharap kahit ikaw mismo ay hindi na makapag-open sa FB account mo. Dahil ang smartphone mo lang ang tanging SUSI para pwede kang makapalog-in sa ibang device or PC dahil yun lang ang nagbibigay sayo ng LOGIN CODES para ikaw ay makapaglog-in sa ibang device. Maliban na lang kung may ginawa kang Recovery Codes.
How to get your Recovery Codes? Refer in the picture below.
After you recieve the Recovey Codes, make sure to keep it in a safe place like by uploading it in a cloud storage if you have, like OneDrive and Google Drive.